The recent announcement about the Copilot Recall feature for PCs, detailed in Microsoft’s blog, caught my attention. Microsoft’s response to user feedback has been impressive, demonstrating their commitment to addressing concerns and improving their offerings. In this post, I’ll delve into the details of the update, the changes made, and why it’s a significant step forward, especially considering the initial backlash.
The Initial Announcement: A Security Fiasco
When Microsoft first introduced Copilot Recall, the concept seemed promising. However, it quickly became apparent that the implementation had severe security flaws. The use of an unencrypted SQLite database to store sensitive user data raised red flags across the tech community. Articles from CNET and Ars Technica highlighted these issues, emphasizing the risks of storing data in plain text accessible to anyone with local access to the system.
Technical Breakdown of the Initial Flaws
- Unencrypted SQLite Database: The SQLite database used to store user data was not encrypted. This meant that any sensitive information stored within the database was in plain text, easily accessible by anyone with local access to the machine. This lack of encryption posed a significant risk of data breaches.
- Inadequate Access Controls: The initial implementation did not have sufficient access control mechanisms. This oversight meant that the database could potentially be accessed by unauthorized users, increasing the risk of data exposure and unauthorized data manipulation.
- Transparency Issues: Microsoft did not initially provide detailed information on how user data was being stored and managed. This lack of transparency led to mistrust and widespread concern among users and security experts.
Ethical Hacker’s Demonstration
To underline the security flaws, an ethical hacker developed an open-source tool named TotalRecall. This tool was designed to extract data from the Copilot Recall SQLite database effortlessly, demonstrating just how vulnerable the system was. The existence of such a tool highlighted the urgency for Microsoft to address these security lapses.
Microsoft’s Response: Listening and Acting
In their latest blog post, Microsoft has addressed these concerns head-on. The most significant changes include:
- Secured-core PCs: All Copilot+ PCs will now be Secured-core PCs. This means they will come with advanced security features designed to protect the firmware, hardware, and operating system from sophisticated attacks. These PCs provide advanced firmware safeguards and dynamic root-of-trust measurement, ensuring comprehensive protection from chip to cloud.
- Microsoft Pluton Security Processor: The Microsoft Pluton security processor will be enabled by default on all Copilot+ PCs. Pluton is a chip-to-cloud security technology that integrates directly into the CPU. It is designed with Zero Trust principles, ensuring that credentials, identities, personal data, and encryption keys are securely stored and significantly harder to extract, even if an attacker has physical access to the PC.
- Windows Hello Enhanced Sign-in Security (ESS): All Copilot+ PCs will ship with Windows Hello ESS. This feature provides more secure biometric sign-ins, eliminating the need for passwords and enhancing overall user security by protecting against spoofing and other forms of biometric hacking.
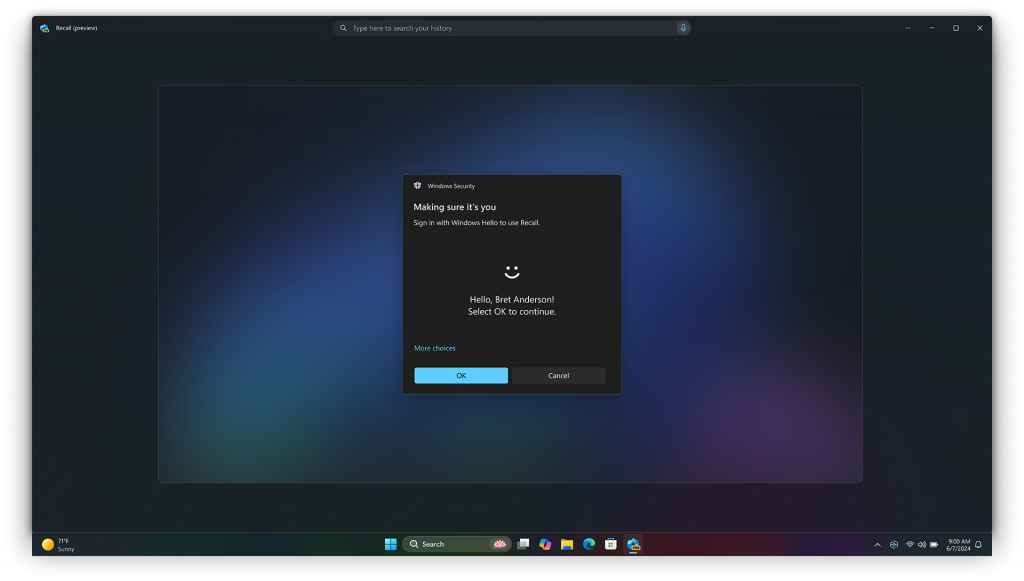
Listening to and Acting on Customer Feedback
Even before making Recall available to customers, Microsoft had already begun listening to user feedback and acting on it. This proactive approach led to several key updates aimed at enhancing user choice and security:
- Opt-In Setup Experience: The setup experience for Copilot+ PCs has been updated to give users a clear choice to opt-in to saving snapshots using Recall. If users do not proactively choose to turn it on, it will be off by default. This ensures that users are fully aware of and in control of their data-saving preferences from the start.
- Windows Hello Enrollment Requirement: To enable Recall, users must enroll in Windows Hello. Additionally, proof of presence is required to view the timeline and search within Recall. This adds an extra layer of security, ensuring that only authenticated users can access their data.
- Just-in-Time Decryption and Enhanced Data Protection: Microsoft has introduced additional layers of data protection, including “just in time” decryption protected by Windows Hello ESS. This means that Recall snapshots will only be decrypted and accessible when the user authenticates, enhancing the security of stored data. Furthermore, the search index database has also been encrypted to protect against unauthorized access.
Why These Changes Matter
The initial rollout of Copilot Recall was a stark reminder of the importance of security in new feature implementations. The use of an unencrypted SQLite database exposed users to potential data breaches. The response from Microsoft, however, has been commendable. By introducing Secured-core PCs, enabling the Microsoft Pluton security processor, and implementing Windows Hello ESS, Microsoft has taken significant steps to enhance the security of Copilot Recall.
These updates demonstrate that Microsoft is willing to acknowledge mistakes and take necessary actions to correct them. The introduction of advanced hardware and firmware security features, coupled with enhanced encryption and access controls, significantly mitigates the risks associated with the initial implementation.
Conclusion
Microsoft’s proactive steps to address the security concerns with Copilot Recall show a commendable commitment to user security and satisfaction. By enhancing encryption, improving access controls, and prioritizing transparency, Microsoft demonstrates a responsive approach that listens to and acts upon user feedback. The latest updates signify a substantial improvement, making Copilot Recall a more secure and reliable feature. It’s encouraging to see Microsoft take such meaningful strides to enhance their product offerings and build trust with their users.